
In the Web User Interface, click the Security tab. In this section you can configure and change the Security settings for the Wireless MAXg Access Point.

You can set the User name and the Password that you will use to log in to the Wireless MAXg Access Point. U.S. Robotics recommends that you create a user name and password so that unauthorised clients cannot log in to the access point and make changes to the settings. The user name and password are case-sensitive.
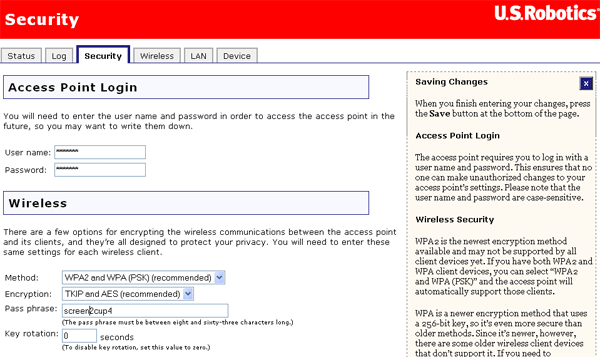
In this section you can enable the wireless security features. U.S. Robotics strongly recommends that you enable some form of wireless security so that unauthorised clients are not able to access your network.
Note: Any changes you make to the security settings of the access point must also be made on all the wireless clients that will connect to the Access Point.
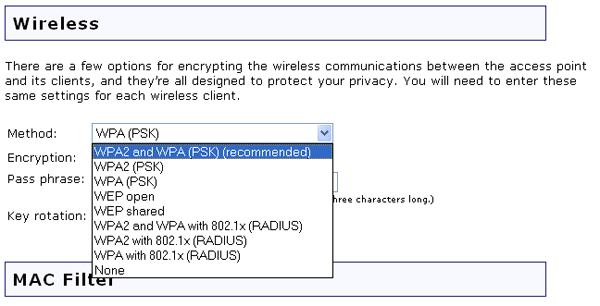
For Method, you can choose one of the following options:
You will have to configure different settings depending upon the option you choose.
WPA's use of keys is very similar to WEP in that encryption security is used for every data transmission and a combination of keys are used to provide access control to a network, but the key is only used once to start the process and is a 256-bit key. Once communication is established, the key will be regularly changed to a random variation of the original key, which provides a higher level of security. U.S. Robotics recommends that you use the most secure mechanism available on your Wireless MAXg Access Point.
Note: If you want to add a wireless device that does not support the WPA security protocol, set the access point to use WEP. U.S. Robotics recommends using the WEP open method with a 128-bitAscii or 128-bithex key type. If the security protocol used by the wireless device does not match the security protocol used by the access point, you will not not be able to connect to the wireless network.
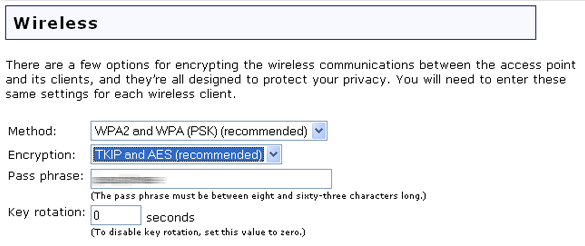
If you enable WPA2 and WPA(PSK) (recommended), WPA2 (PSK) , or WPA (PSK), you will need to select an Encryption type. You can select either TKIP and AES (recommended), AES, or TKIP. You will then need to enter a Pass phrase. The pass phrase must be at least eight characters in length and must be the same on each computer that is connected to the wireless network. You can also set the Key rotation in seconds. The WPA and WPA2 security protocols use pairwise keys for unicast packets and group keys for multicast packets. Key rotation specifies how often the access point generates a new group key for broadcast and multicast packets. TKIP (Temporal Key Integrity Protocol) scrambles the keys using a hashing algorithm and ensures that the keys haven’t been tampered with by adding an integrity-checking feature. AES (Advanced Encryption Standard) is a symmetric key encryption technique.
WEP is an encryption scheme that is used to protect your wireless data communications. WEP uses a combination of 64-bit keys or 128-bit keys to provide access control to your network and encryption security for every data transmission. To decode a data transmission, each wireless client on the network must use an identical 64-bit or 128-bit key.
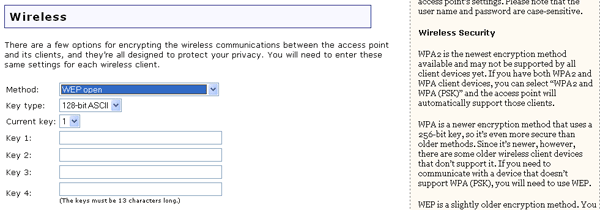
If you enable WEP open or WEP shared, you will need to select the length of the Key type from 128-bit ASCII, 128-bit hexadecimal, 64-bit ASCII, or 64-bit hexadecimal.
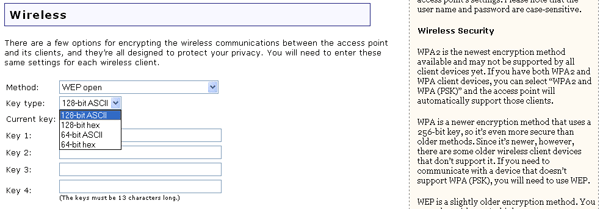
The Key type options provide the different levels of WEP security for your network, 64-bit being the lowest and 128-bit being the highest. Hexadecimal values are defined as A-F and 0-9 while ASCII uses all alphanumeric characters.
If you enable WEP, you are allowed to store up to four Keys. You must select the one to use in the Current key dropdown menu. The following table details the necessary length of characters that must be input for each WEP key that is activated.
| Hex | ASCII | |
|---|---|---|
| 64-bit | 10 characters | 5 characters |
| 128-bit | 26 characters | 13 characters |
802.1x (RADIUS) authentication is primarily an option that only businesses will use where the users are authenticated through a central server.
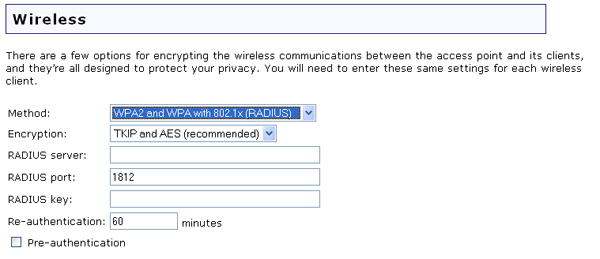
If you select WPA2 and WPA with 802.1x (RADIUS), WPA2 with 802.1x (RADIUS), or WPA with 802.1x (RADIUS), you will then need to provide the information for RADIUS Server. This is the computer to which the Wireless MAXg Access Point creates a secure connection and authenticates a wireless user or connection. You will need to supply the IP address of the RADIUS Server. You also need to supply a RADIUS Port or use the default 1812. Next, you will need to provide the RADIUS Key. This can be a word or a set of numbers and is used as an additional form of security between the RADIUS server and the access point. Re-authentication determines how often the access point sends a message and require the clients to respond with the correct security information. Finally, you can select Pre-authentication. When enabled, Pre-authentication allows authentication of a wireless client on other wireless access points in its range while it is still communicating through its current wireless access point.
You can select None and have no wireless encryption enabled for your network.
Note: This is not recommended since without any encryption enabled, your network will be vulnerable to outside malicious attacks.
In this area you can control which wireless devices are allowed or denied access to the Wireless MAXg Access Point based upon their MAC addresses. The MAC address can usually be found either on a label on the external wireless product or in the configuration utility of the wireless client, depending on the wireless device you are using.
You can click Allow Current Clients and all of the wireless clients
that are currently connected to the Wireless MAXg Access Point will be allowed access
to the access point in the future.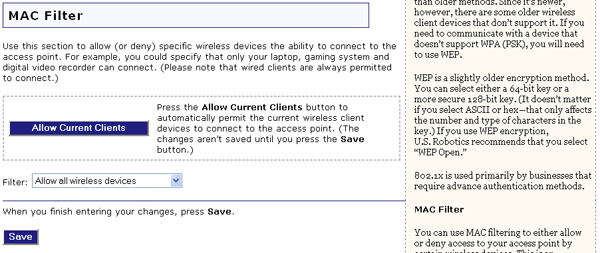
If you would rather configure this option on a more individual basis, you can select either Allow all wireless devices, Allow only these wireless devices, or Deny only these wireless devices.
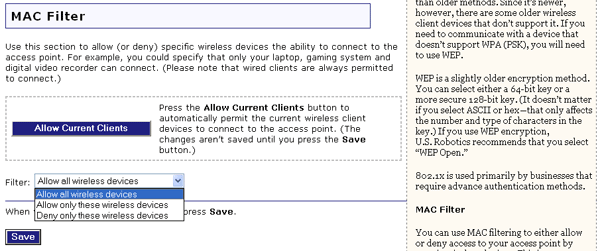
After making any changes to the configuration options or security settings of the Wireless MAXg Access Point, you must click Save in order for your changes to be saved and implemented.